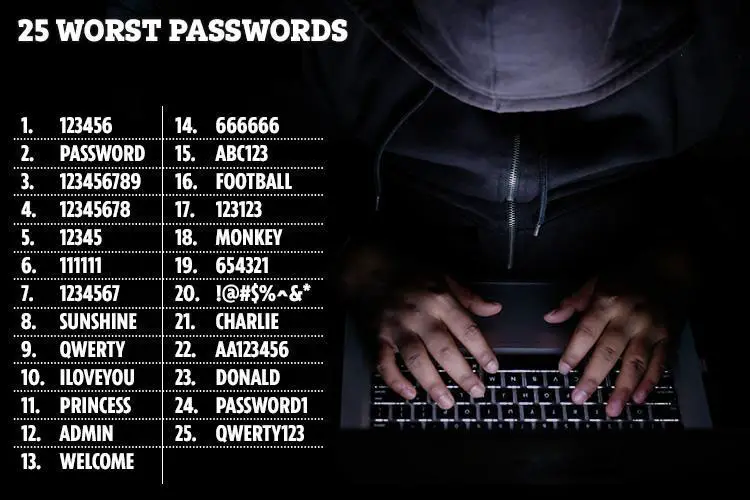
Password Encryption Presentation
| Introduction to Password Encryption | ||
|---|---|---|
| Password encryption is a crucial security measure used to protect sensitive information. Encryption converts plain text passwords into unreadable formats. The purpose of password encryption is to prevent unauthorized access and ensure data confidentiality. | ||
| 1 | ||
| Types of Password Encryption Algorithms | ||
|---|---|---|
| Hash-based encryption algorithms are commonly used for password encryption. Secure Hash Algorithm (SHA-2) is a widely used hash function for password encryption. Advanced Encryption Standard (AES) is another popular algorithm for password encryption. | ||
| 2 | ||
| Benefits of Password Encryption | ||
|---|---|---|
| Password encryption provides an additional layer of security beyond basic password storage. Encrypted passwords make it difficult for attackers to reverse engineer and obtain the original password. Even if the encrypted password is compromised, it is challenging to decrypt without the encryption key. | ||
| 3 | ||
| Best Practices for Password Encryption | ||
|---|---|---|
| Use strong encryption algorithms with long hash lengths for better security. Implement salting techniques to add randomness and complexity to encrypted passwords. Regularly update and strengthen encryption methods to keep up with evolving security threats. | ||
| 4 | ||
| Common Password Encryption Vulnerabilities | ||
|---|---|---|
| Weak encryption algorithms can be prone to brute-force attacks. Lack of salt usage makes password encryption susceptible to precomputed tables. Inadequate encryption key management can lead to compromised passwords. | ||
| 5 | ||
| Considerations for Implementing Password Encryption | ||
|---|---|---|
| Choose a password encryption algorithm that meets the specific security requirements of your system. Ensure that encryption keys are properly managed and protected. Regularly review and update password encryption practices to stay ahead of emerging threats. | ||
| 6 | ||
| Summary and Key Takeaways | ||
|---|---|---|
| Password encryption is essential for safeguarding sensitive data. Use strong encryption algorithms and implement additional security measures like salting. Regularly update and review password encryption methods to stay ahead of potential vulnerabilities. | ||
| 7 | ||
| References (download PPTX file for details) | ||
|---|---|---|
| Doe, J. (2020). Password Encryption: Best Pra... Smith, A. (2019). Understanding Password Encr... Johnson, M. (2018). Common Vulnerabilities in... |  | |
| 8 | ||