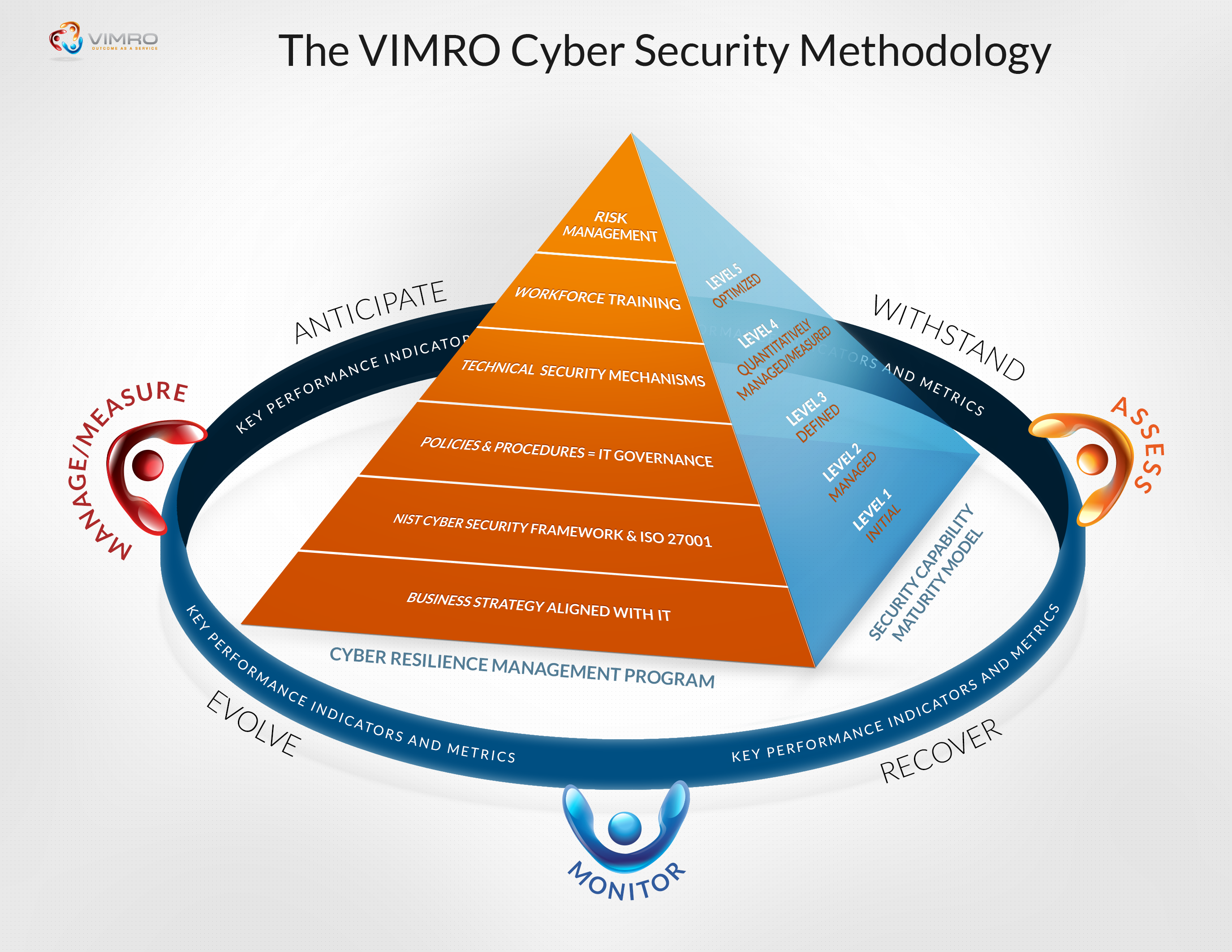
Network Traffic Analysis In Cyber Security Presentation
| Introduction to Network Traffic Analysis in Cyber Security | ||
|---|---|---|
| Network Traffic Analysis is the process of monitoring, capturing, and analyzing network data to identify potential security threats and vulnerabilities. It plays a crucial role in detecting and preventing cyber attacks. By analyzing network traffic, security professionals can gain insights into malicious activities, unusual behavior, and potential indicators of compromise. | ||
| 1 | ||
| Importance of Network Traffic Analysis | ||
|---|---|---|
| Network Traffic Analysis helps in identifying and mitigating various types of cyber threats, such as malware infections, data breaches, and DDoS attacks. It provides visibility into network activities, allowing organizations to monitor and control the flow of data. By analyzing traffic patterns, security teams can detect anomalies and take proactive measures to safeguard the network. | ||
| 2 | ||
| Benefits of Network Traffic Analysis | ||
|---|---|---|
| Early threat detection: Network Traffic Analysis enables the identification of potential threats at an early stage, minimizing the impact of an attack. Incident response: By analyzing network traffic, cyber security experts can investigate incidents, track the source of an attack, and respond effectively. Forensic analysis: Network Traffic Analysis provides valuable data for forensic investigations, helping to reconstruct events and gather evidence. | ||
| 3 | ||
| Techniques Used in Network Traffic Analysis | ||
|---|---|---|
| Packet capture and analysis: This technique involves capturing packets from the network and analyzing their contents to identify anomalies or malicious activities. Protocol analysis: It involves examining network protocols to understand how data is transmitted and identify any abnormalities or vulnerabilities. Flow analysis: Flow analysis focuses on the behavior of network traffic flows, identifying patterns and anomalies that could indicate a security threat. |  | |
| 4 | ||
| Tools and Technologies for Network Traffic Analysis | ||
|---|---|---|
| Intrusion Detection Systems (IDS): IDS tools monitor network traffic for suspicious activities and generate alerts when potential threats are detected. Network Traffic Analyzers: These tools collect and analyze network traffic data, providing insights into network behavior and potential security risks. Machine Learning and AI: These technologies are increasingly used in network traffic analysis to detect and predict abnormal behavior and potential threats. |  | |
| 5 | ||
| Challenges in Network Traffic Analysis | ||
|---|---|---|
| Encryption: The widespread use of encryption makes it difficult to analyze the contents of network traffic, leading to potential blind spots for security teams. Volume and complexity: The sheer volume and complexity of network traffic data can make analysis challenging, requiring advanced tools and techniques. False positives: Network Traffic Analysis may generate false positives, requiring skilled analysts to differentiate between genuine threats and normal network behavior. |  | |
| 6 | ||
| Best Practices for Network Traffic Analysis | ||
|---|---|---|
| Continuous monitoring: Implementing a continuous monitoring strategy ensures that network traffic is constantly analyzed for potential threats. Baseline creation: Establishing a baseline of normal network behavior helps in identifying anomalies and suspicious activities. Collaboration: Encouraging collaboration between security teams and sharing information enhances the effectiveness of network traffic analysis. | ||
| 7 | ||
| Case Study: Network Traffic Analysis in Action | ||
|---|---|---|
| Provide a real-world example of how network traffic analysis helped detect and mitigate a cyber attack. Highlight the key steps taken during the analysis process and the eventual outcome. Your third bullet | ||
| 8 | ||
| Conclusion | ||
|---|---|---|
| Network Traffic Analysis is a critical component of cyber security, enabling organizations to detect and respond to potential threats. By analyzing network traffic patterns and behaviors, organizations can enhance their security posture and protect their critical assets. Implementing best practices and utilizing advanced tools and technologies can significantly improve the effectiveness of network traffic analysis. | ||
| 9 | ||
| References (download PPTX file for details) | ||
|---|---|---|
| Include a list of credible sources and refere... Your second bullet... Your third bullet... |  | |
| 10 | ||