Cyber Security Presentation
| Introduction to Cyber Security | ||
|---|---|---|
| Cyber security is the practice of protecting computers, servers, mobile devices, electronic systems, networks, and data from digital threats. The importance of cyber security has increased due to the rise of cybercrime and the growing reliance on technology in our daily lives. Cyber security involves the implementation of measures to prevent, detect, and respond to cyber threats. | ||
| 1 | ||
| Types of Cyber Threats | ||
|---|---|---|
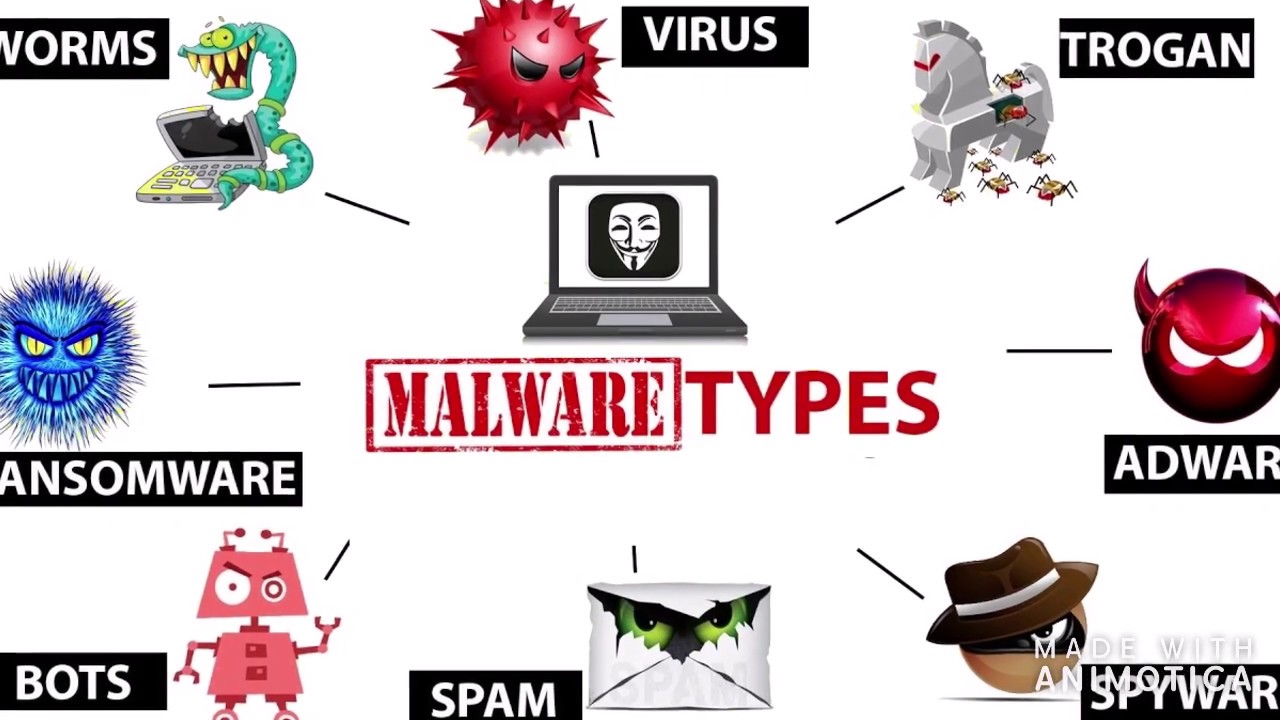
| Malware, such as viruses, worms, trojans, ransomware, and spyware, can infect and damage computers or steal sensitive information. Phishing attacks use deceptive emails or websites to trick users into revealing personal information, passwords, or financial details. Denial of Service (DoS) attacks overwhelm a network or website, making it inaccessible to users. | ||
| 2 | ||
| Importance of Cyber Security | ||
|---|---|---|
| Cyber security protects sensitive information, such as personal data, financial records, and intellectual property, from unauthorized access or theft. It ensures the continuity of business operations by safeguarding critical systems and preventing disruptions. Cyber security builds trust among users, customers, and stakeholders, enhancing the reputation and credibility of organizations. | ||
| 3 | ||
| Best Practices for Cyber Security | ||
|---|---|---|
| Regularly update software and operating systems to patch vulnerabilities and protect against known exploits. Use strong, unique passwords for all accounts and enable two-factor authentication whenever possible. Be cautious when clicking on links or downloading attachments from unknown or suspicious sources. | ||
| 4 | ||
| Importance of Employee Training | ||
|---|---|---|
| Educating employees on cyber security best practices helps prevent social engineering attacks and reduces the risk of human error. Training should cover topics such as recognizing phishing emails, creating secure passwords, and identifying suspicious online behavior. Regularly updating employees on emerging cyber threats and providing ongoing education ensures a proactive approach to cyber security. | ||
| 5 | ||
| Network Security Measures | ||
|---|---|---|
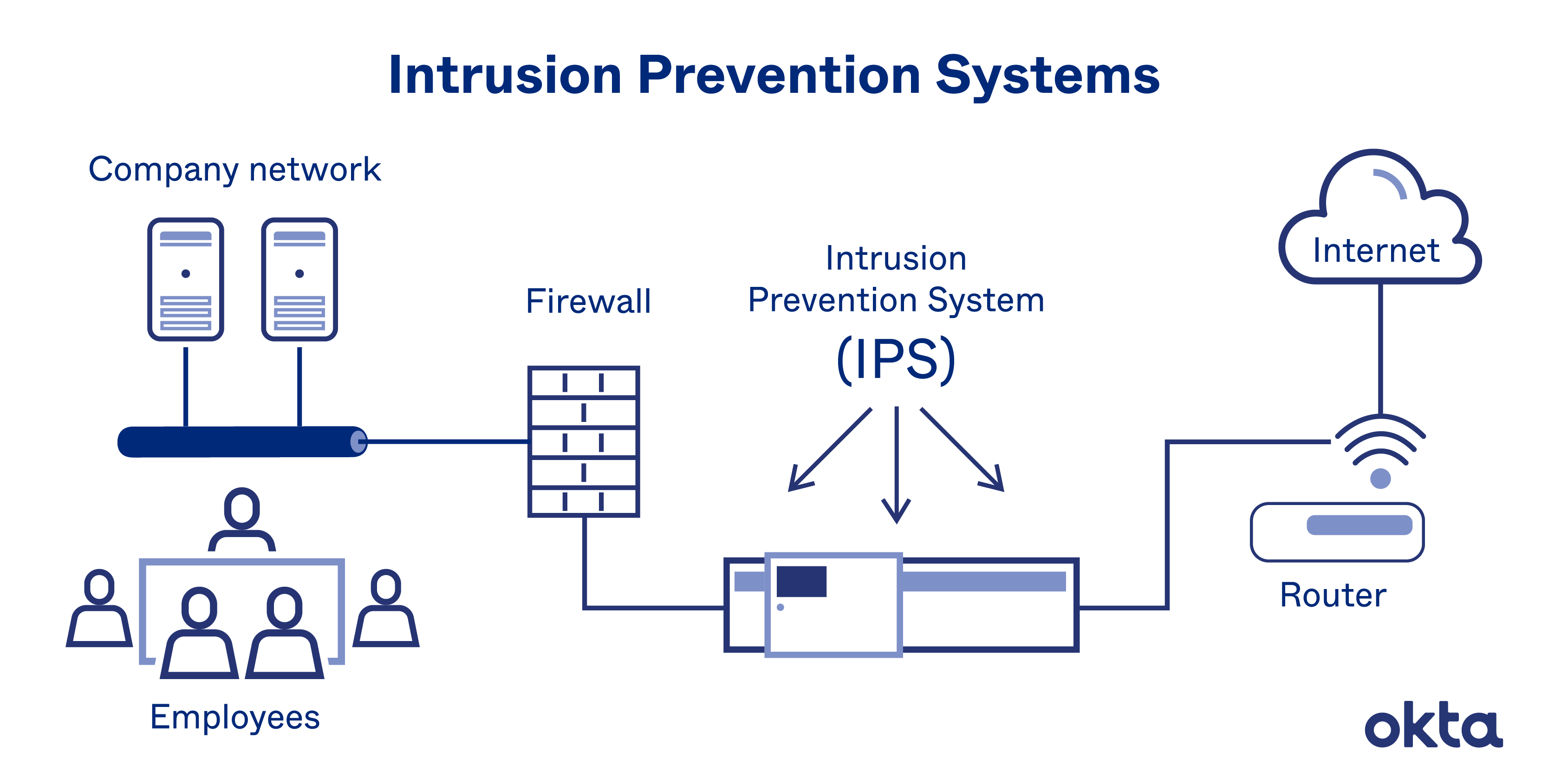
| Implementing firewalls, intrusion detection systems (IDS), and intrusion prevention systems (IPS) helps protect networks from unauthorized access and suspicious activities. Using virtual private networks (VPNs) encrypts internet connections, ensuring secure communication and data transmission. Regularly conducting vulnerability assessments and penetration testing helps identify and address network weaknesses. | ||
| 6 | ||
| Importance of Data Encryption | ||
|---|---|---|
| Data encryption converts sensitive information into unreadable code, making it inaccessible to unauthorized individuals. Encrypting data at rest, in transit, and in storage ensures the confidentiality and integrity of information. Implementing strong encryption algorithms and key management practices is crucial to maintain data security. | ||
| 7 | ||
| Incident Response and Recovery | ||
|---|---|---|
| Developing an incident response plan helps organizations effectively respond to and mitigate cyber security incidents. Regularly backing up data and testing restoration processes ensures quick recovery in case of data loss or system compromise. Conducting post-incident analysis and learning from past incidents helps improve future incident response capabilities. | ||
| 8 | ||
| Emerging Trends in Cyber Security | ||
|---|---|---|
| Artificial Intelligence (AI) and Machine Learning (ML) are being used to enhance threat detection and response capabilities. Internet of Things (IoT) devices pose new challenges as they increase the attack surface and require robust security measures. Cloud security is becoming increasingly important as more organizations adopt cloud-based services and storage. | ||
| 9 | ||
| Conclusion | ||
|---|---|---|
| Cyber security is a critical aspect of protecting digital assets and ensuring the safety and privacy of individuals and organizations. By staying informed about emerging threats and implementing best practices, we can effectively mitigate cyber risks. Collaboration between individuals, organizations, and governments is crucial to build a secure and resilient cyber ecosystem. | ||
| 10 | ||