Hacker Presentation
| Introduction to Hackers | ||
|---|---|---|
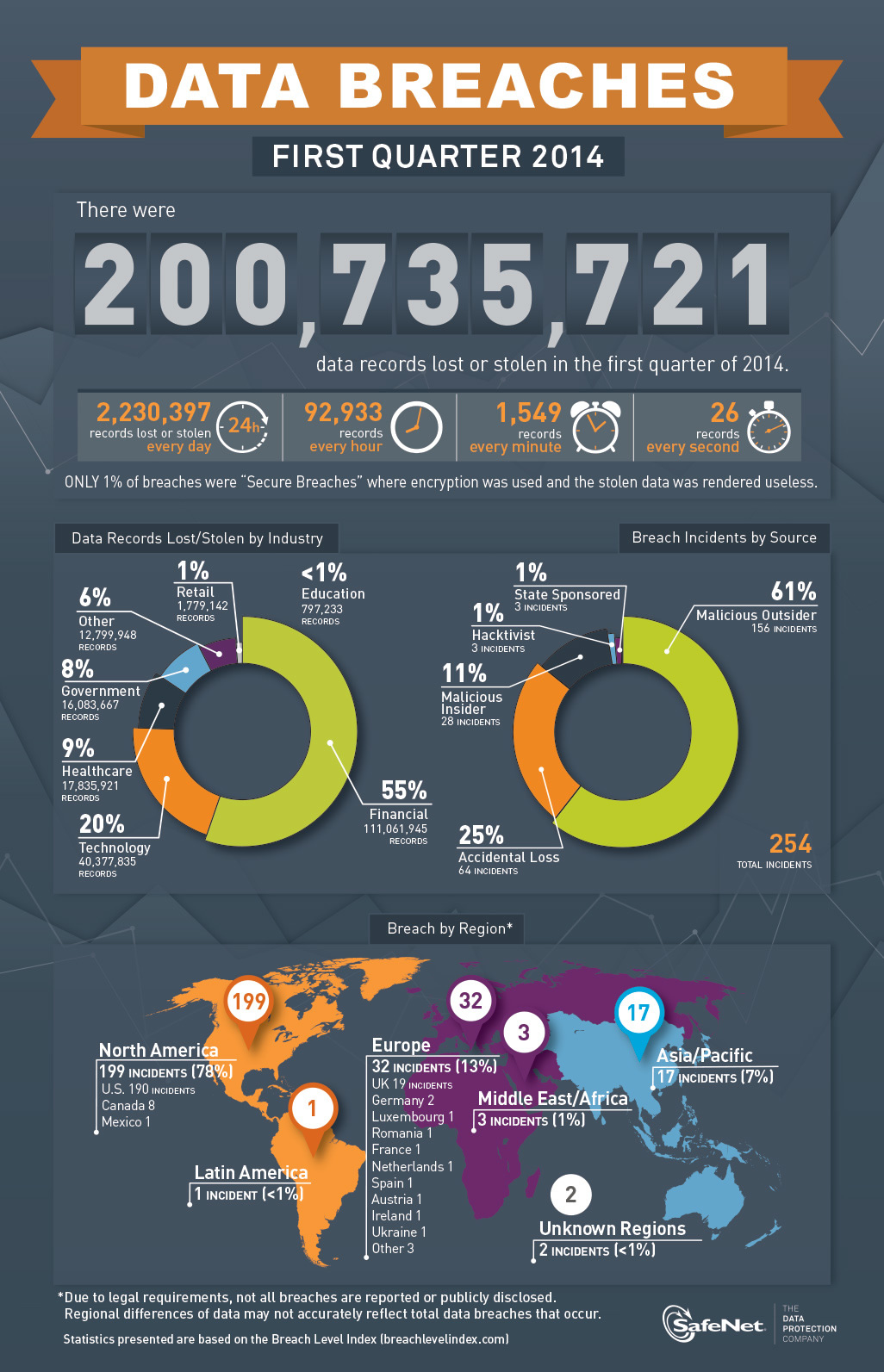
| Hackers are skilled individuals who use their knowledge of computer systems to gain unauthorized access. They can be categorized as ethical or malicious, depending on their intentions and actions. Hacking can involve various techniques such as phishing, malware, or brute force attacks. | ||
| 1 | ||
| Types of Hackers | ||
|---|---|---|
| White Hat Hackers, also known as ethical hackers, work to identify vulnerabilities in systems and help organizations improve their security. Black Hat Hackers engage in illegal activities and exploit vulnerabilities for personal gain. Grey Hat Hackers fall in between, as they may perform unauthorized activities to expose security flaws but without malicious intent. | ||
| 2 | ||
| Motivations for Hacking | ||
|---|---|---|
| Financial gain is a common motivation for hackers, as they may steal sensitive information or engage in cyber-espionage. Hacktivism refers to hackers who aim to promote a specific cause or ideology by targeting organizations or governments. Some hackers hack for personal satisfaction, seeking the challenge and thrill of outsmarting security systems. | ||
| 3 | ||
| Common Hacking Techniques | ||
|---|---|---|
| Phishing involves tricking individuals into revealing sensitive information through deceptive emails or websites. Malware, such as viruses or ransomware, is used to gain unauthorized access, steal data, or disrupt systems. Brute force attacks involve repeatedly trying different combinations of usernames and passwords until the correct one is found. | ||
| 4 | ||
| Hacking Tools and Exploits | ||
|---|---|---|
| Hackers utilize various tools like network scanners, password crackers, and vulnerability scanners to identify weaknesses. Exploits are software vulnerabilities that hackers exploit to gain unauthorized access or control over a system. Social engineering techniques, such as manipulating individuals into revealing passwords, are also commonly used. | ||
| 5 | ||
| Cybersecurity Measures | ||
|---|---|---|
| Organizations implement firewalls, intrusion detection systems, and antivirus software to protect against hacking attempts. Regular software updates and patches help to address security vulnerabilities. Employee training and awareness programs play a crucial role in preventing successful hacking attempts. | ||
| 6 | ||
| Legal and Ethical Implications | ||
|---|---|---|
| Hacking is illegal in most jurisdictions, and hackers can face severe legal consequences. Ethical concerns arise when hackers expose vulnerabilities without authorization or cause harm to innocent individuals or organizations. The line between ethical hacking and illegal activities can be subjective and requires clear ethical guidelines. | ||
| 7 | ||
| Impact of Hacking | ||
|---|---|---|
| Hacking can lead to financial losses for individuals and organizations due to data breaches or system disruptions. It can damage an organization's reputation, leading to a loss of trust from customers and partners. Hacking can also have far-reaching consequences, such as affecting critical infrastructure or compromising national security. | ||
| 8 | ||
| Protecting Against Hackers | ||
|---|---|---|
| Strong and unique passwords, along with two-factor authentication, help protect against unauthorized access. Regular data backups ensure that data can be restored in case of a successful attack. Encrypting sensitive data and using secure protocols can make it harder for hackers to intercept or access information. | ||
| 9 | ||
| Conclusion | ||
|---|---|---|
| Hackers are skilled individuals who can pose a significant threat to individuals and organizations. Understanding their motivations, techniques, and the importance of cybersecurity measures is crucial in defending against hacking attempts. By staying informed and implementing security best practices, individuals and organizations can mitigate the risks of hacking. | ||
| 10 | ||
| References (download PPTX file for details) | ||
|---|---|---|
| Title of Book/ Article, Author's Name, Publis... Title of Website/ Page, Website Name, URL, Ac... Your third bullet... |  | |
| 11 | ||