Ethical Hacking Presentation
| Introduction to Ethical Hacking | ||
|---|---|---|
| Ethical hacking, also known as penetration testing or white-hat hacking, is the practice of identifying vulnerabilities in computer systems and networks. Ethical hackers use their skills and knowledge to assess the security of an organization's infrastructure and provide recommendations for improvement. By conducting ethical hacking, organizations can proactively address potential weaknesses and prevent unauthorized access or data breaches. | ||
| 1 | ||
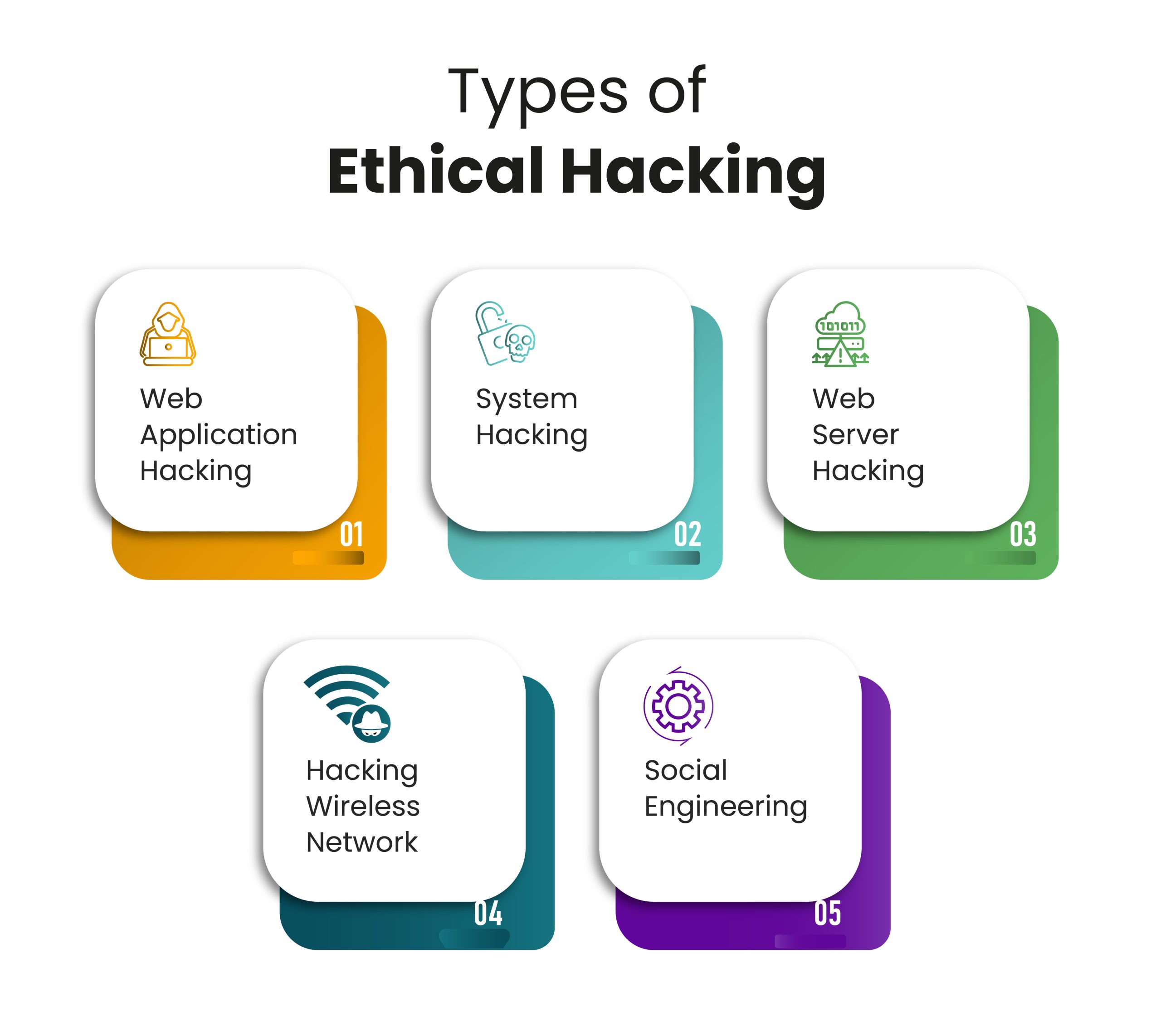
| Types of Ethical Hacking | ||
|---|---|---|
| Network Hacking: Evaluating the security of network devices, such as routers and switches, to identify vulnerabilities and potential entry points. Web Application Hacking: Assessing the security of web applications, including identifying vulnerabilities in code, authentication mechanisms, and input validation. Wireless Network Hacking: Testing the security of Wi-Fi networks, including encryption protocols, access controls, and wireless devices. | ||
| 2 | ||
| Ethical Hacking Methodology | ||
|---|---|---|
| Reconnaissance: Gathering information about the target system or network using various techniques, such as open-source intelligence (OSINT) and scanning. Vulnerability Assessment: Identifying vulnerabilities in the target system or network using tools and techniques like port scanning, vulnerability scanning, and penetration testing. Exploitation: Attempting to exploit the identified vulnerabilities to gain unauthorized access or perform other malicious activities. | ||
| 3 | ||
| Legal and Ethical Considerations | ||
|---|---|---|
| Ethical hackers must abide by legal and ethical guidelines, such as obtaining proper authorization before initiating any testing. Unauthorized hacking is illegal and can lead to severe legal consequences. Ethical hackers should always prioritize the confidentiality, integrity, and availability of the systems they are testing and respect privacy rights. | ||
| 4 | ||
| Tools Used in Ethical Hacking | ||
|---|---|---|
| Nessus: A popular vulnerability scanning tool that helps identify vulnerabilities in the target system or network. Metasploit: A framework used for developing and executing exploits, as well as conducting post-exploitation activities. Wireshark: A network protocol analyzer used for capturing and analyzing network traffic to detect any vulnerabilities or security issues. | ||
| 5 | ||
| Benefits of Ethical Hacking | ||
|---|---|---|
| Identifying and fixing vulnerabilities before malicious hackers can exploit them, reducing the risk of data breaches and financial loss. Enhancing the overall security posture of an organization's systems and networks. Meeting regulatory compliance requirements by conducting regular security assessments. | ||
| 6 | ||
| Challenges in Ethical Hacking | ||
|---|---|---|
| Keeping up with rapidly evolving technologies and new attack vectors. Balancing the need for thorough testing with the potential disruption or damage to the target system or network. Maintaining ethical standards and ensuring responsible disclosure of vulnerabilities to the organization. | ||
| 7 | ||
| Ethical Hacking Certifications | ||
|---|---|---|
| Certified Ethical Hacker (CEH): A widely recognized certification that validates the skills and knowledge of ethical hackers. Offensive Security Certified Professional (OSCP): A hands-on certification that demonstrates proficiency in penetration testing and ethical hacking techniques. GIAC Penetration Tester (GPEN): A certification that focuses on identifying and exploiting vulnerabilities in target systems. | ||
| 8 | ||
| Ethical Hacking Best Practices | ||
|---|---|---|
| Obtain proper authorization from the organization before conducting any testing. Document all activities, findings, and recommendations in a comprehensive report. Continuously update skills and knowledge through training, certifications, and participation in the security community. | ||
| 9 | ||
| Conclusion | ||
|---|---|---|
| Ethical hacking plays a crucial role in identifying and addressing vulnerabilities in computer systems and networks. By conducting ethical hacking, organizations can proactively protect their assets and prevent potential data breaches. Ethical hackers should always operate within legal and ethical boundaries, prioritizing the security and privacy of the systems they are testing. | ||
| 10 | ||
| References (download PPTX file for details) | ||
|---|---|---|
| EC-Council. (n.d.). Certified Ethical Hacker ... Offensive Security. (n.d.). Offensive Securit... SANS Institute. (n.d.). GIAC Penetration Test... |  | |
| 11 | ||