DoS Attack Using NS 2 Presentation
| Introduction | ||
|---|---|---|
| A Denial of Service (DoS) attack is a malicious attempt to disrupt the normal functioning of a network. NS 2 is a widely used network simulation tool that allows researchers to study the behavior of networks. This presentation will explore how NS 2 can be used to simulate and analyze DoS attacks. | ||
| 1 | ||
| Understanding DoS Attacks | ||
|---|---|---|
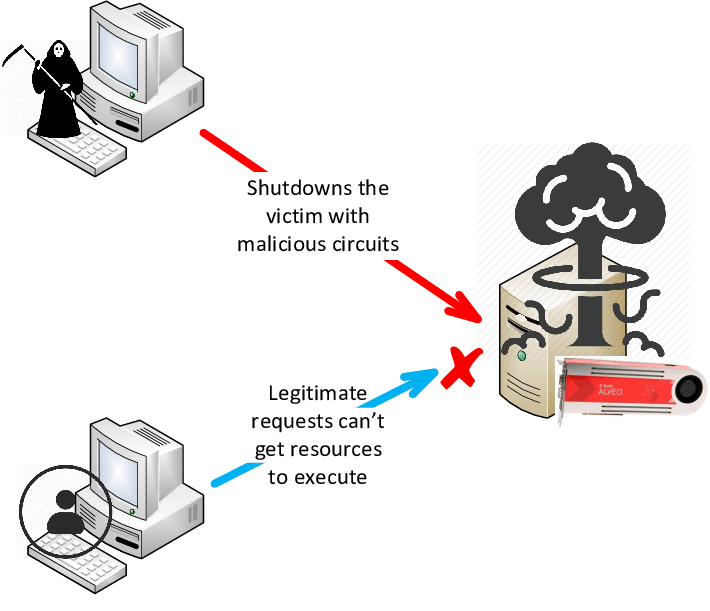
| A DoS attack floods a network or system with excessive traffic, overwhelming its capacity to respond. This leads to a denial of service for legitimate users, causing network slowdowns or complete unavailability. DoS attacks can target various layers of the network, including the application layer, transport layer, or network layer. | ||
| 2 | ||
| Types of DoS Attacks | ||
|---|---|---|
| TCP SYN Flood: Exploits the TCP handshake process by sending a flood of SYN requests, exhausting server resources. UDP Flood: Inundates a target with a high volume of UDP packets, overwhelming the network or system. ICMP Flood: Utilizes ICMP Echo Requests (ping) to flood a target, consuming network bandwidth and resources. | ||
| 3 | ||
| Conducting DoS Attacks in NS 2 | ||
|---|---|---|
| NS 2 provides a framework to simulate DoS attacks by generating excessive traffic towards a target node. The attacker can be modeled as a malicious node that floods the network with packets, emulating a DoS attack. Various parameters can be adjusted, such as the packet rate, packet size, and attack duration, to study different scenarios. | ||
| 4 | ||
| Impact of DoS Attacks | ||
|---|---|---|
| DoS attacks can disrupt critical services, causing financial losses, reputation damage, and customer dissatisfaction. Network performance degradation and increased response time are common consequences of DoS attacks. Analyzing the impact of DoS attacks in NS 2 helps in developing effective defense mechanisms and mitigations. | ||
| 5 | ||
| Defense Mechanisms | ||
|---|---|---|
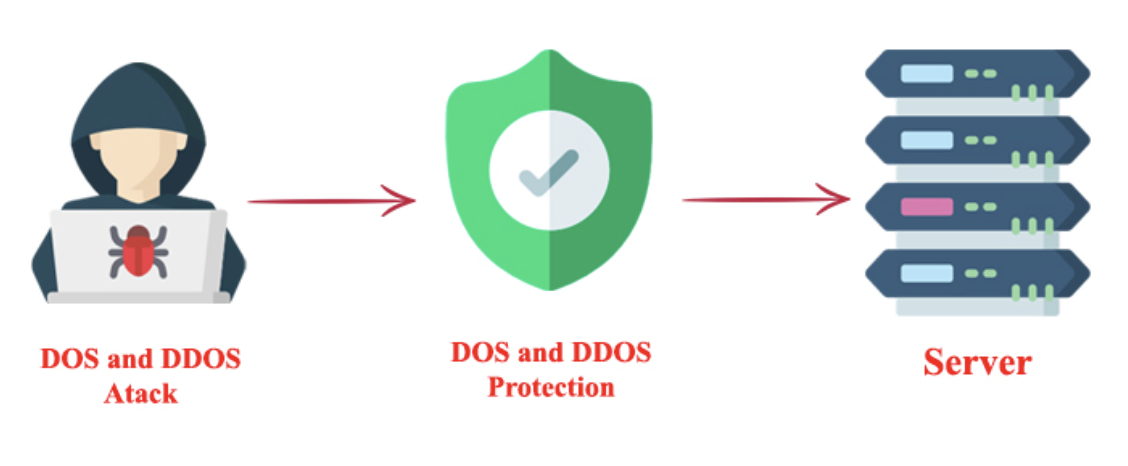
| Intrusion Detection Systems (IDS): Monitor network traffic and identify patterns indicative of a DoS attack. Rate Limiting: Imposes limits on the number of packets a node can send, preventing excessive traffic. Traffic Filtering: Filters out malicious packets using firewalls or access control lists (ACLs). | ||
| 6 | ||
| Mitigation Techniques | ||
|---|---|---|
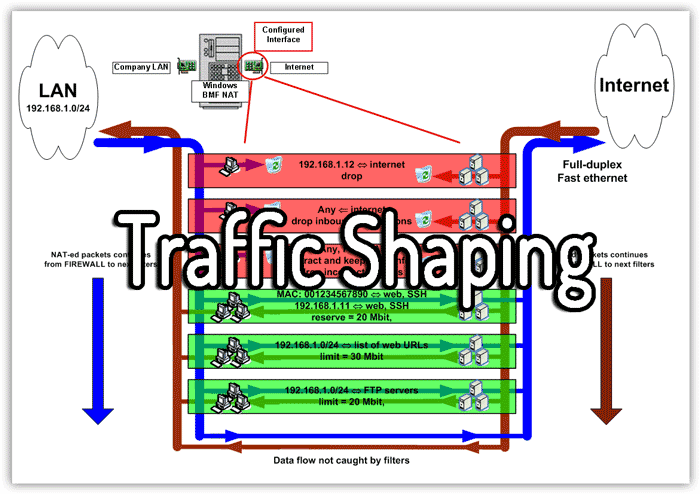
| Traffic Shaping: Prioritizes network traffic to ensure critical services receive sufficient bandwidth during an attack. Load Balancing: Distributes traffic across multiple servers, reducing the impact of a DoS attack on individual nodes. Anomaly Detection: Utilizes machine learning algorithms to detect abnormal network behavior and identify potential DoS attacks. | ||
| 7 | ||
| Simulating DoS Attacks in NS 2 | ||
|---|---|---|
| NS 2 allows researchers to analyze the behavior of DoS attacks under controlled conditions. Simulations can help in understanding attack patterns, evaluating defense mechanisms, and testing mitigation techniques. The results obtained from NS 2 simulations can guide the development of more robust and secure network infrastructures. | ||
| 8 | ||
| Conclusion | ||
|---|---|---|
| NS 2 provides a powerful platform for simulating and studying DoS attacks in various network scenarios. Understanding the impact of DoS attacks and testing defense mechanisms in NS 2 can help in building more resilient networks. Continued research and development in this area are crucial to stay ahead of evolving DoS attack techniques. | ||
| 9 | ||
| Questions? | ||
|---|---|---|
| Thank you for your attention. Any questions regarding DoS attacks using NS 2 are welcome. Your second bullet Your third bullet | ||
| 10 | ||