AWS Cyber Security Presentation
| Introduction to AWS Cyber Security | ||
|---|---|---|
| AWS Cyber Security is a comprehensive solution that ensures the protection of your data and applications on the AWS platform. AWS offers a wide range of security services and features designed to meet various compliance requirements and protect against cyber threats. With AWS Cyber Security, you can have peace of mind knowing that your infrastructure is safeguarded against unauthorized access and potential attacks. | ||
| 1 | ||
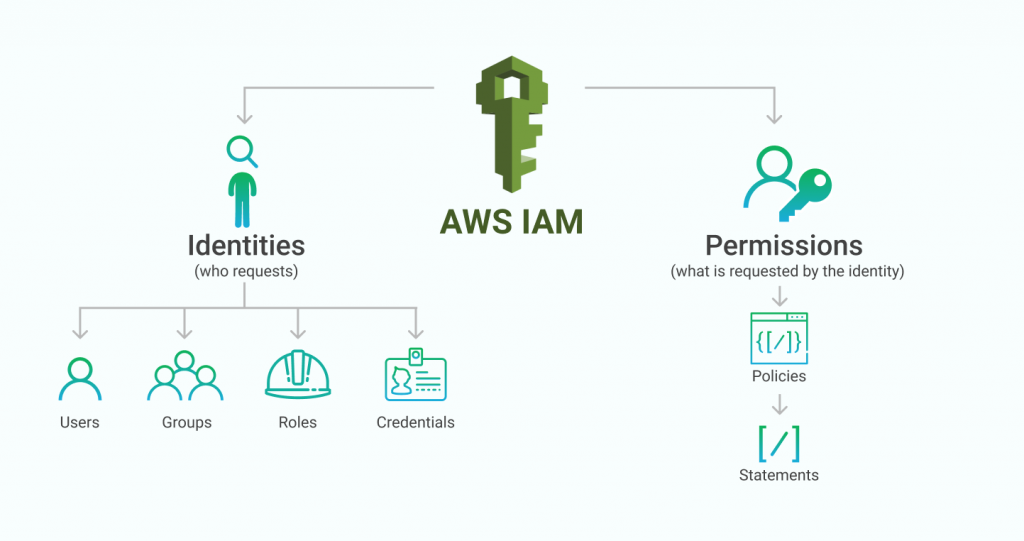
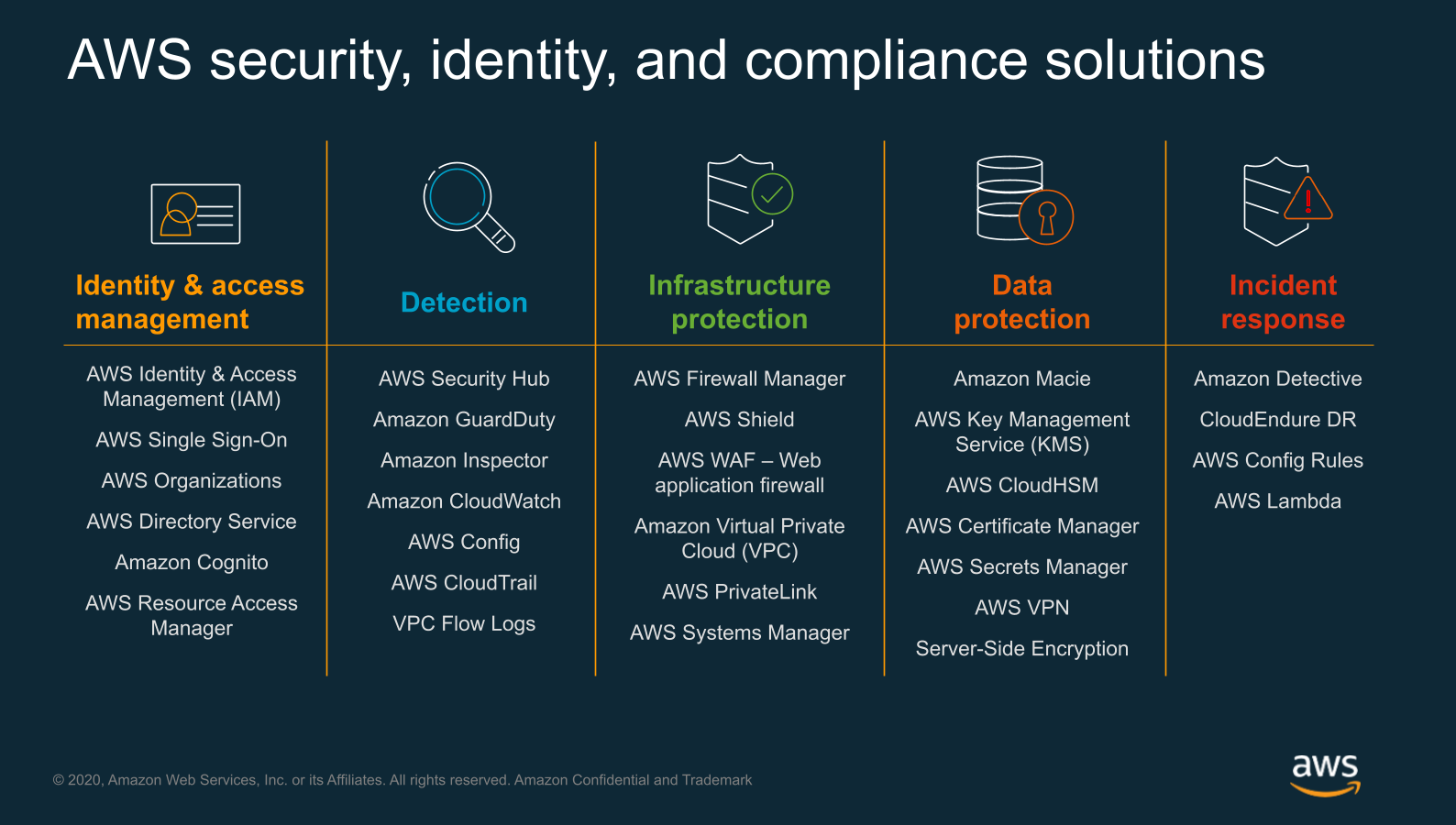
| AWS Identity and Access Management (IAM) | ||
|---|---|---|
| IAM allows you to manage user access and permissions to AWS resources. With IAM, you can create and manage users, groups, and roles, ensuring that only authorized individuals have access to your AWS resources. IAM also supports multi-factor authentication (MFA), adding an extra layer of security to user accounts. | ||
| 2 | ||
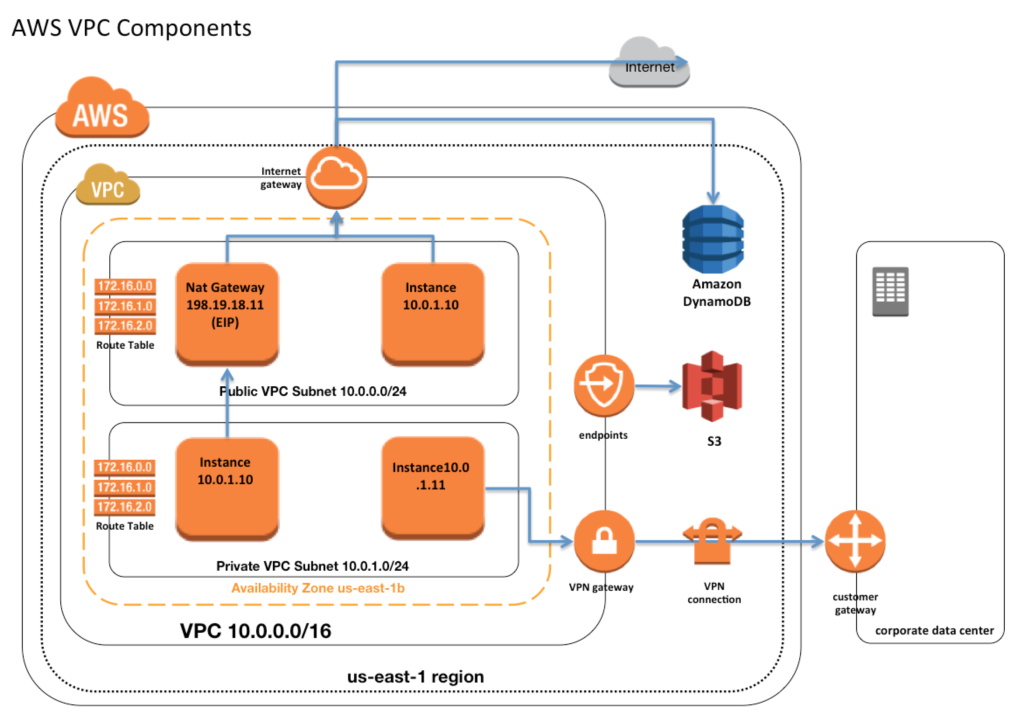
| AWS Virtual Private Cloud (VPC) | ||
|---|---|---|
| VPC enables you to create a private network within the AWS cloud. With VPC, you can define your own IP address range, subnets, and network gateways, providing isolation and control over your resources. VPC also allows you to set up network access control lists (ACLs) and security groups to restrict inbound and outbound traffic. | ||
| 3 | ||
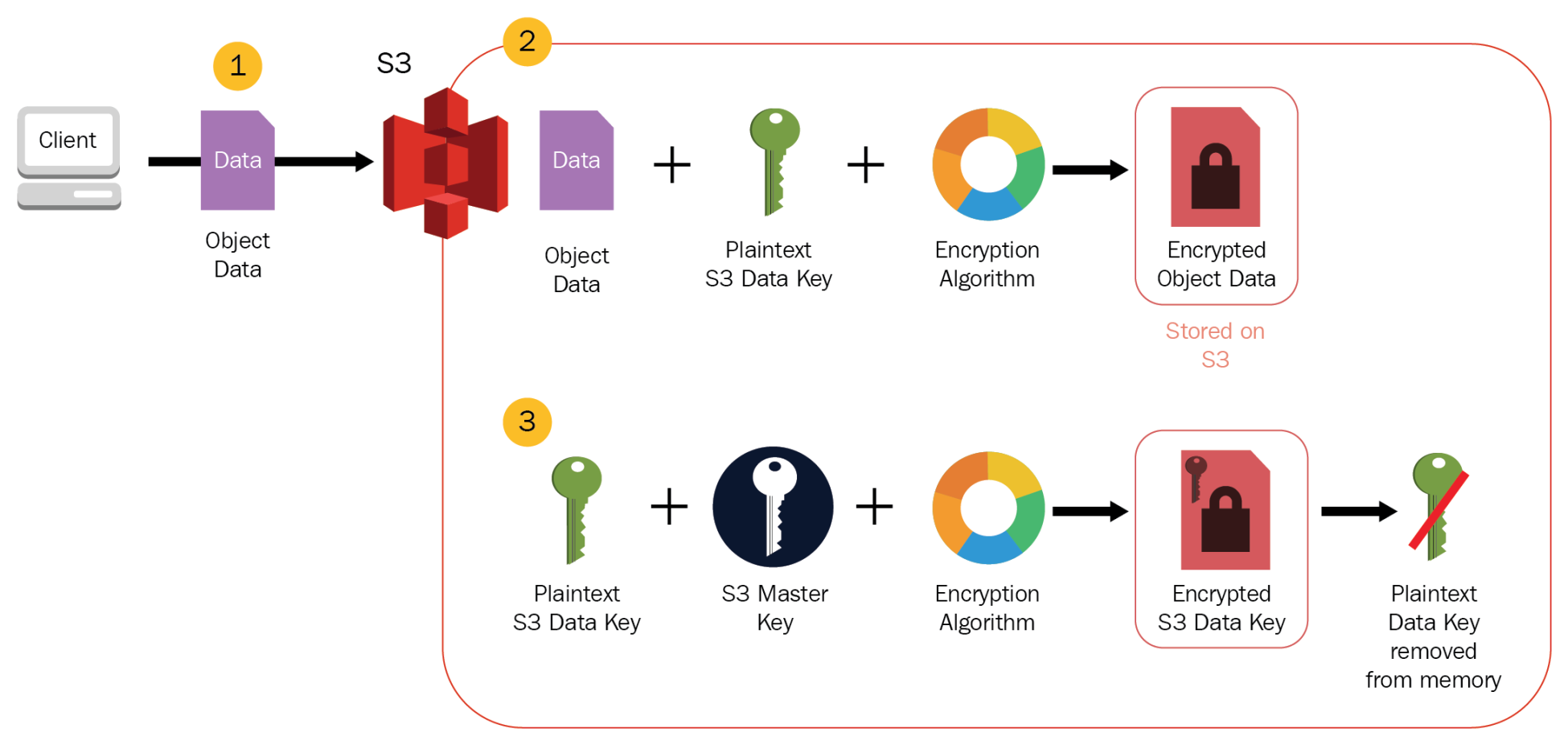
| AWS Encryption Services | ||
|---|---|---|
| AWS offers various encryption services to protect your data at rest and in transit. Amazon S3 provides server-side encryption, allowing you to encrypt your data using AWS-managed keys or your own keys. AWS Key Management Service (KMS) enables you to centrally manage and control the encryption keys used by AWS services and your own applications. | ||
| 4 | ||
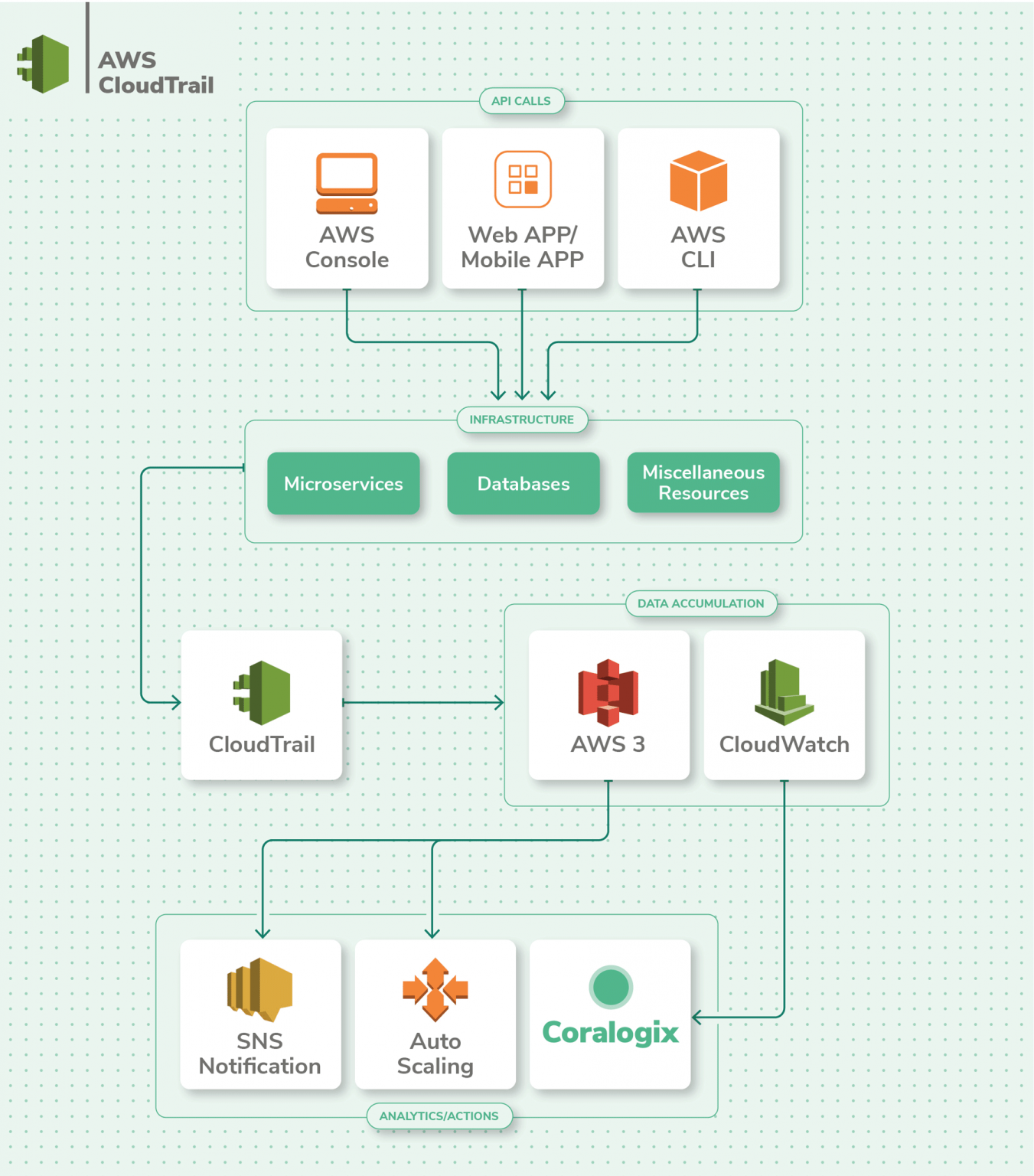
| AWS Monitoring and Logging | ||
|---|---|---|
| AWS CloudTrail captures API calls and events for auditing and compliance purposes. Amazon GuardDuty monitors your AWS accounts for malicious activity and helps detect potential threats. AWS CloudWatch provides centralized logging and monitoring for your AWS resources, allowing you to set alarms and gain insights into your system's performance. | ||
| 5 | ||
| AWS DDoS Protection | ||
|---|---|---|
| AWS Shield provides protection against Distributed Denial of Service (DDoS) attacks, automatically detecting and mitigating common attack patterns. AWS Shield Advanced offers enhanced DDoS protection with advanced threat intelligence and real-time telemetry. With AWS Shield, your applications and data are protected from disruption caused by DDoS attacks. | ||
| 6 | ||
| AWS Compliance and Certifications | ||
|---|---|---|
| AWS has a wide range of compliance certifications, including SOC 1, SOC 2, ISO 27001, and PCI DSS. These certifications ensure that AWS complies with industry standards and best practices for data security and privacy. AWS provides compliance resources and audit reports to help customers meet their own compliance requirements. | ||
| 7 | ||
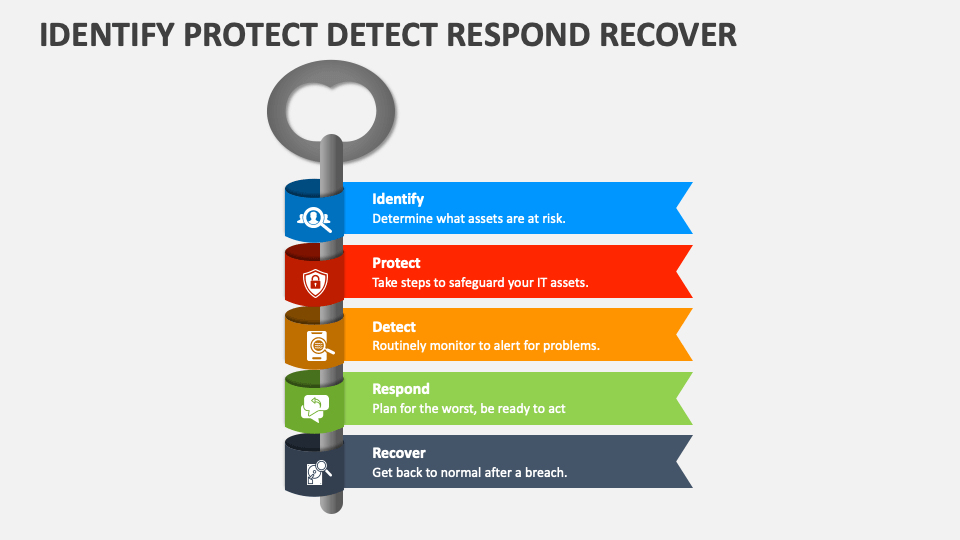
| AWS Incident Response | ||
|---|---|---|
| AWS provides tools and services to help you detect, respond to, and recover from security incidents. AWS Incident Response Services offer guidance and support during security incidents, helping you minimize the impact and restore normal operations. AWS Well-Architected Framework provides best practices and architectural guidance for building secure and resilient applications on AWS. | ||
| 8 | ||
| AWS Shared Responsibility Model | ||
|---|---|---|
| AWS follows a shared responsibility model, where AWS is responsible for the security of the cloud infrastructure, and customers are responsible for securing their applications and data. AWS provides the necessary tools and services to help customers meet their security requirements, but it's important for customers to understand their responsibilities. By following best practices and leveraging AWS security features, customers can build secure and compliant applications on the AWS platform. |  | |
| 9 | ||
| Conclusion | ||
|---|---|---|
| AWS Cyber Security offers a comprehensive set of tools and services to protect your data and applications in the cloud. With features like IAM, VPC, encryption services, monitoring, and DDoS protection, AWS provides a robust security foundation. By understanding and adhering to the shared responsibility model, customers can leverage AWS to build secure and resilient applications. | ||
| 10 | ||